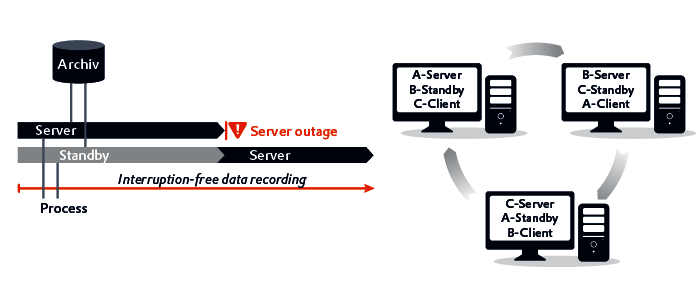
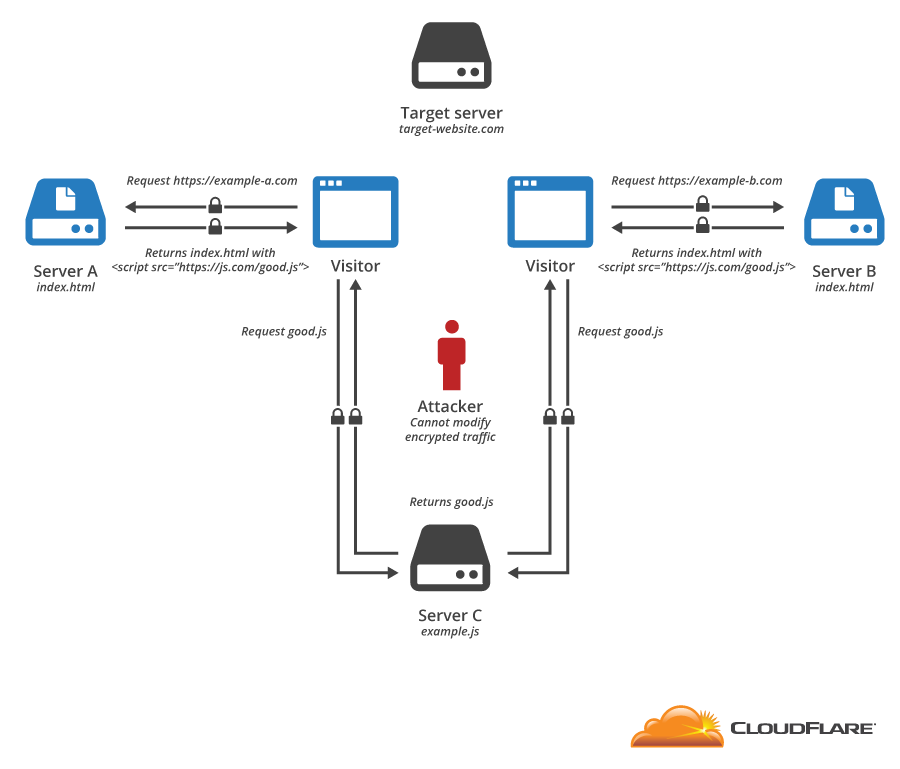
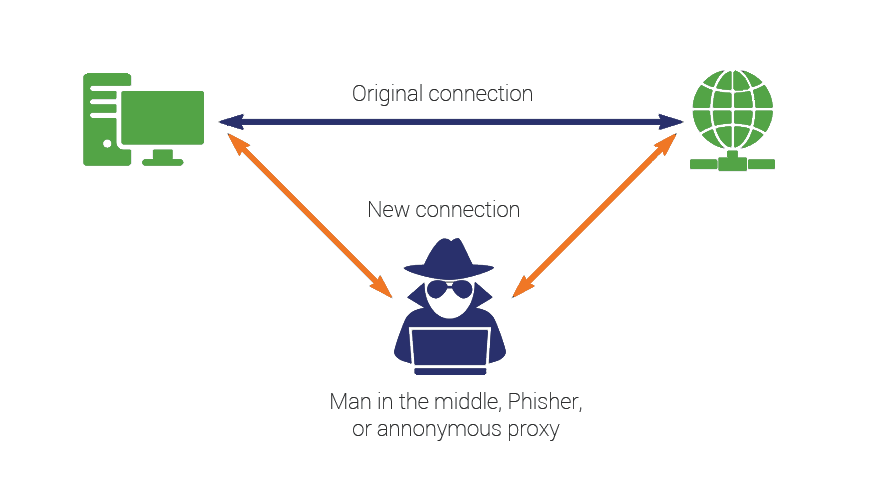
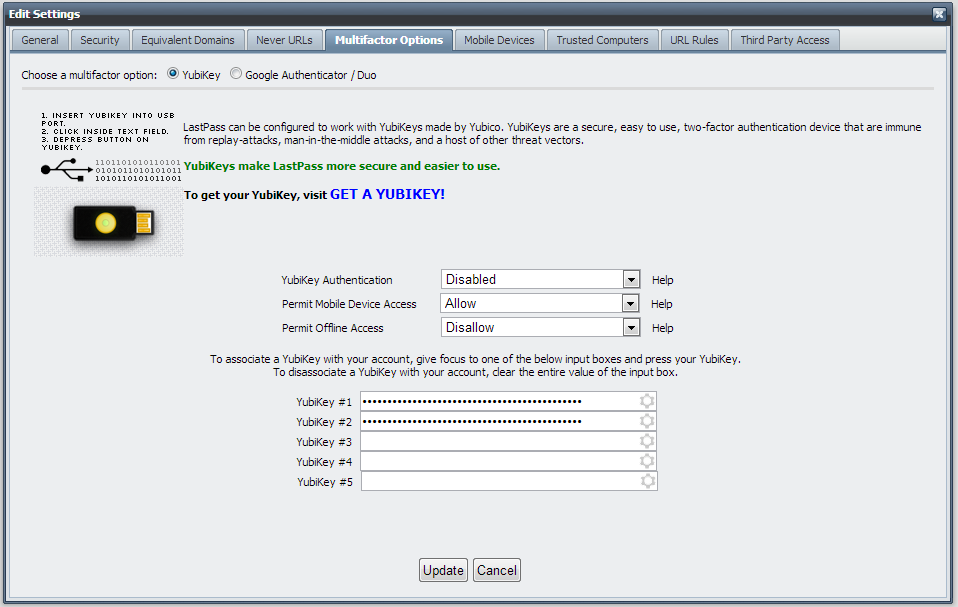
Protocol-level attacks: (a) Man-in-the-middle attack, (b) Brute forcing... | Download Scientific Diagram
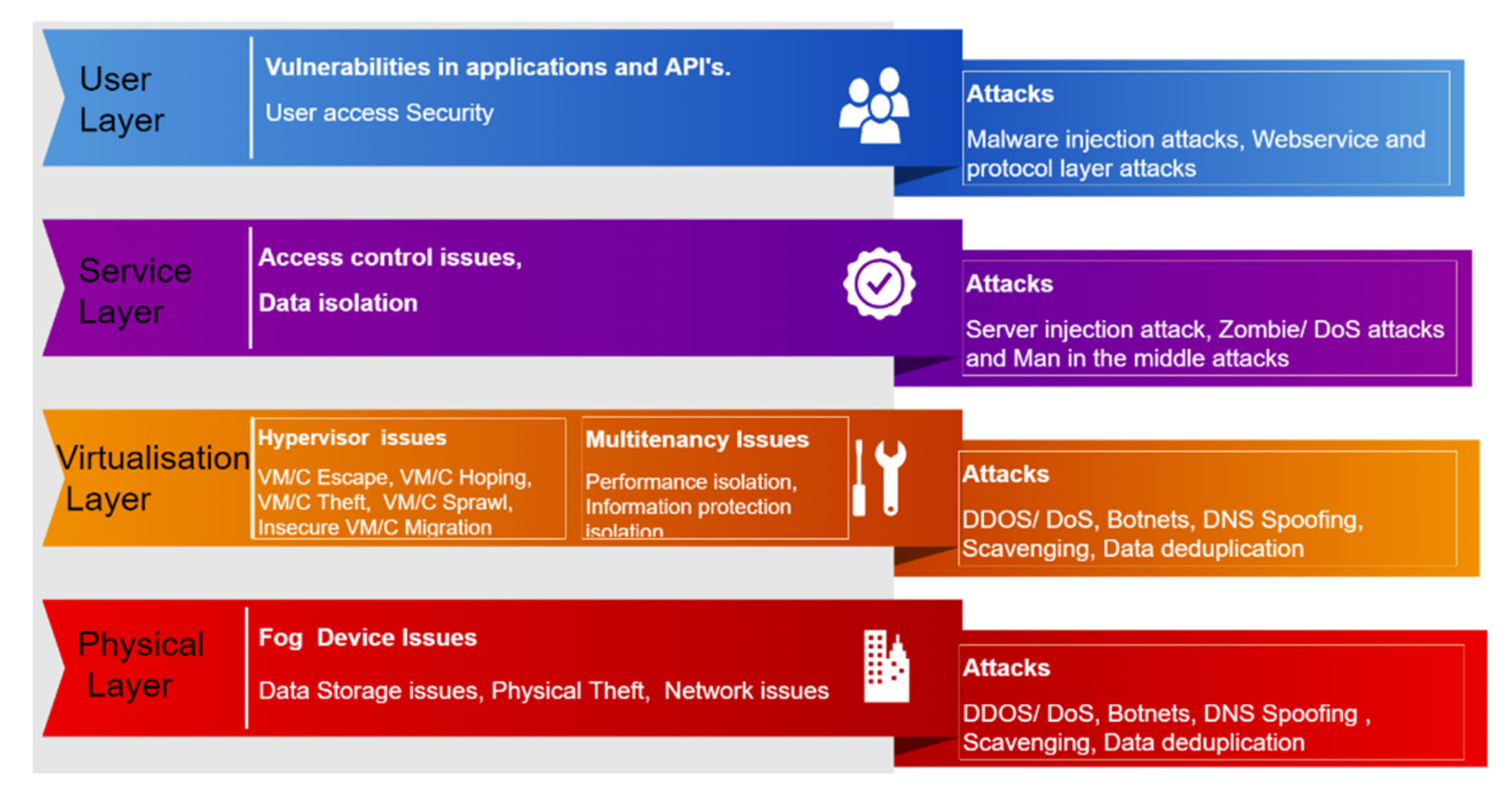
Sensors | Free Full-Text | An Improved ID-Based Data Storage Scheme for Fog-Enabled IoT Environments | HTML
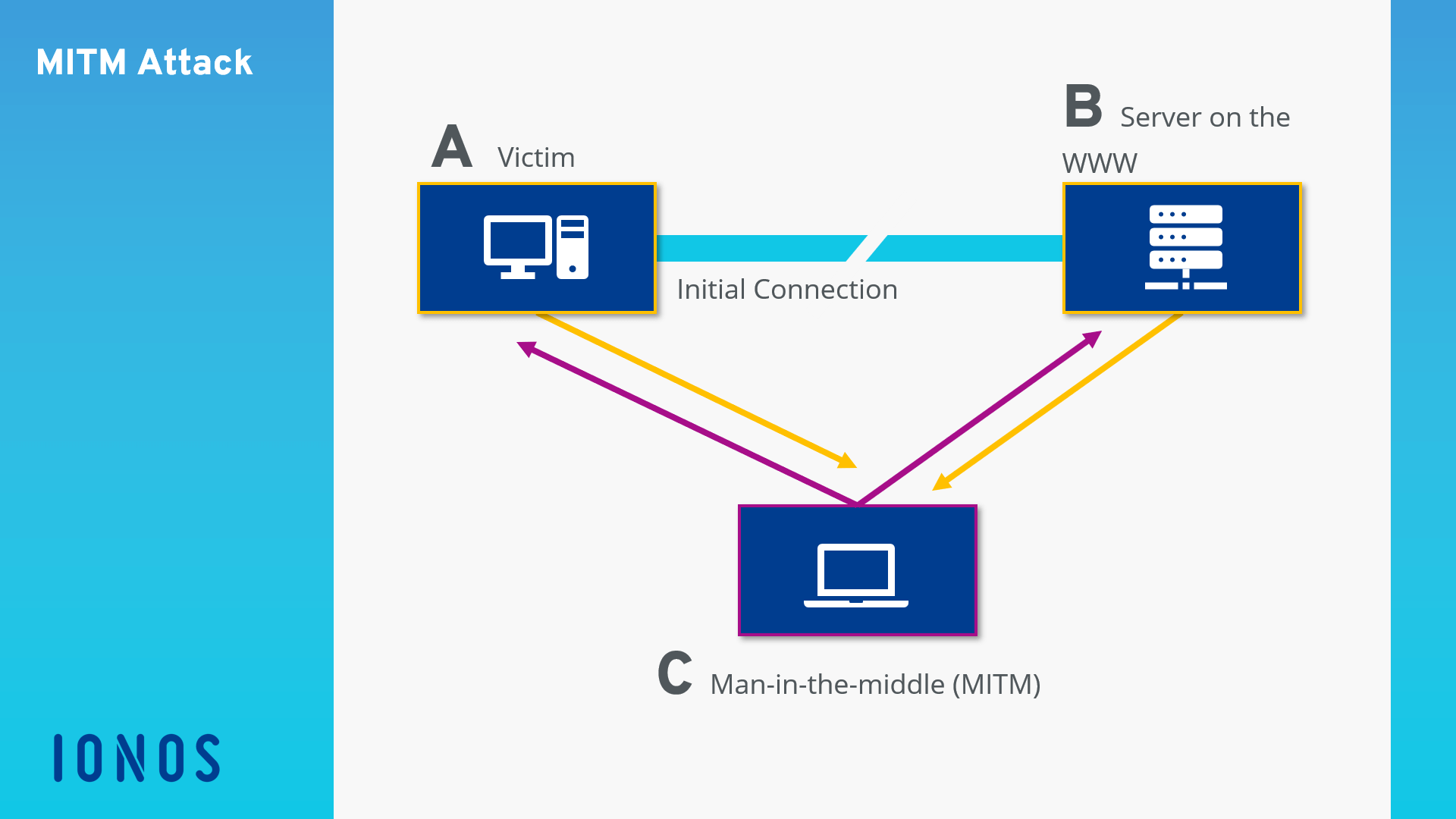
Mobile Critters: Part 1. Man In The Middle Attack. by Kaymera - secure calls & encrypted messages for you and your team